Ensuring WordPress security is more crucial than ever. According to w3techs, WordPress already accounts for 63% of the managed websites market share.
This widespread use of WordPress presents a lucrative target for malicious actors employing automated tools (bots) to identify vulnerabilities and perform attacks.
As highlighted by Imperva’s 10th annual Bad Bot Report, this past year the percentage of non-human traffic has significantly increased, with Bad Bot automated traffic reaching 30% all traffic:
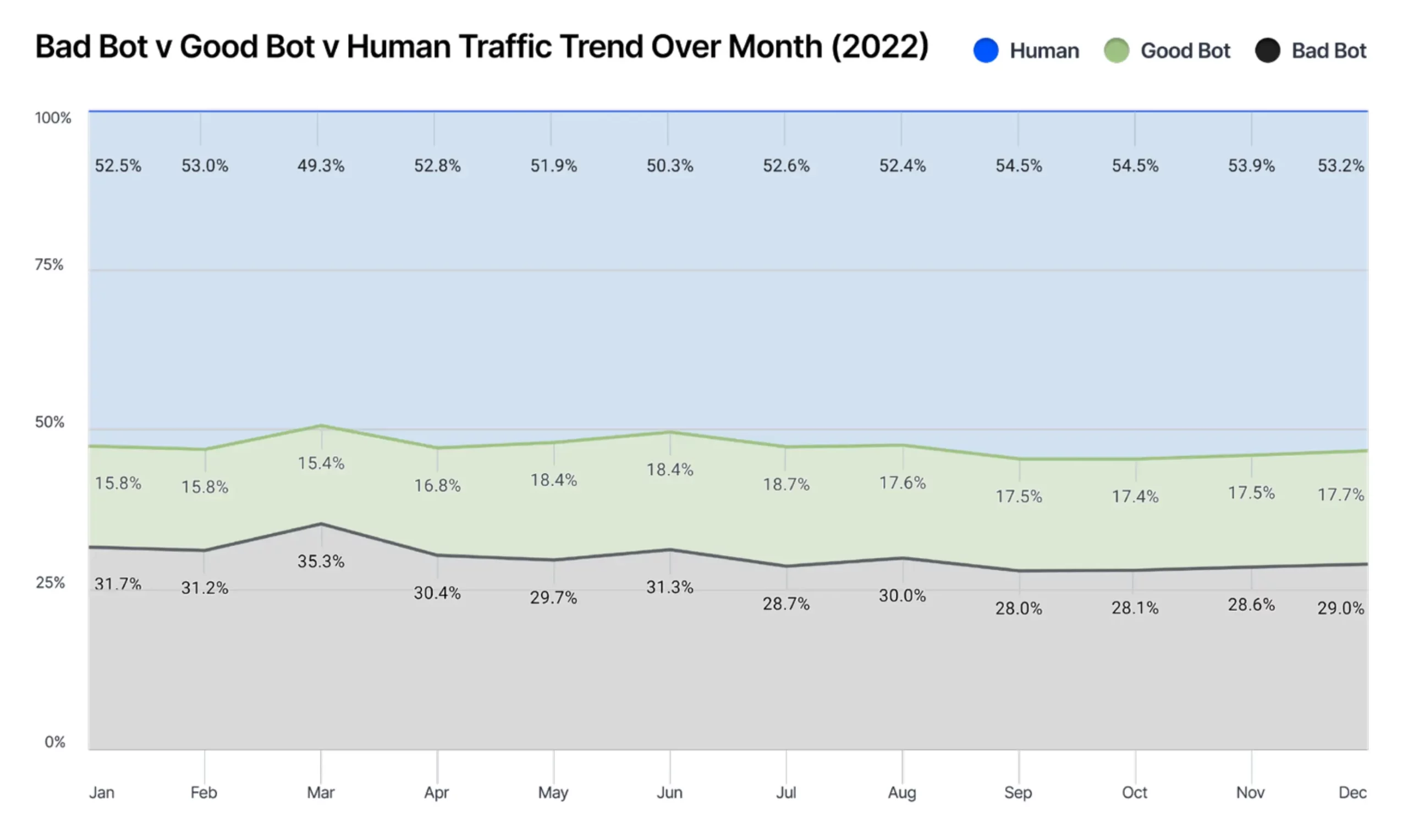
But don’t get scared! Wetopi firewall infrastructure is designed to shield you from these bad actors.
In this post we describe the strategies deployed in our Wetopi Firewall Infrastructure to protect your site.
How to block bot traffic in WordPress
There are a few plugins for WordPress capable of filtering traffic, including WordFence, iThemes Security, All In One WP Security & Firewall, etc. However, their major problem is efficiency. Why?
WordPress is not designed to filter traffic!
WordPress firewall plugins rely on the PHP engine and database. Although they are effective in filtering, due to their resource consumption, they cannot do it efficiently, especially under the pressure of an attack.
If you want your WordPress site to work fast, you cannot delegate such an intensive task as managing the control of every traffic request.
At Wetopi, we handle this task by providing an infrastructure equipped with front-end firewalls specifically designed for WordPress security.
Infrastructure Firewall for WordPress
Filtering and blocking traffic tasks are done in the front firewalls. Always in a previous stage, before reaching your WordPress server. Furthermore, these firewalls are redundant in each of the multiple access networks.
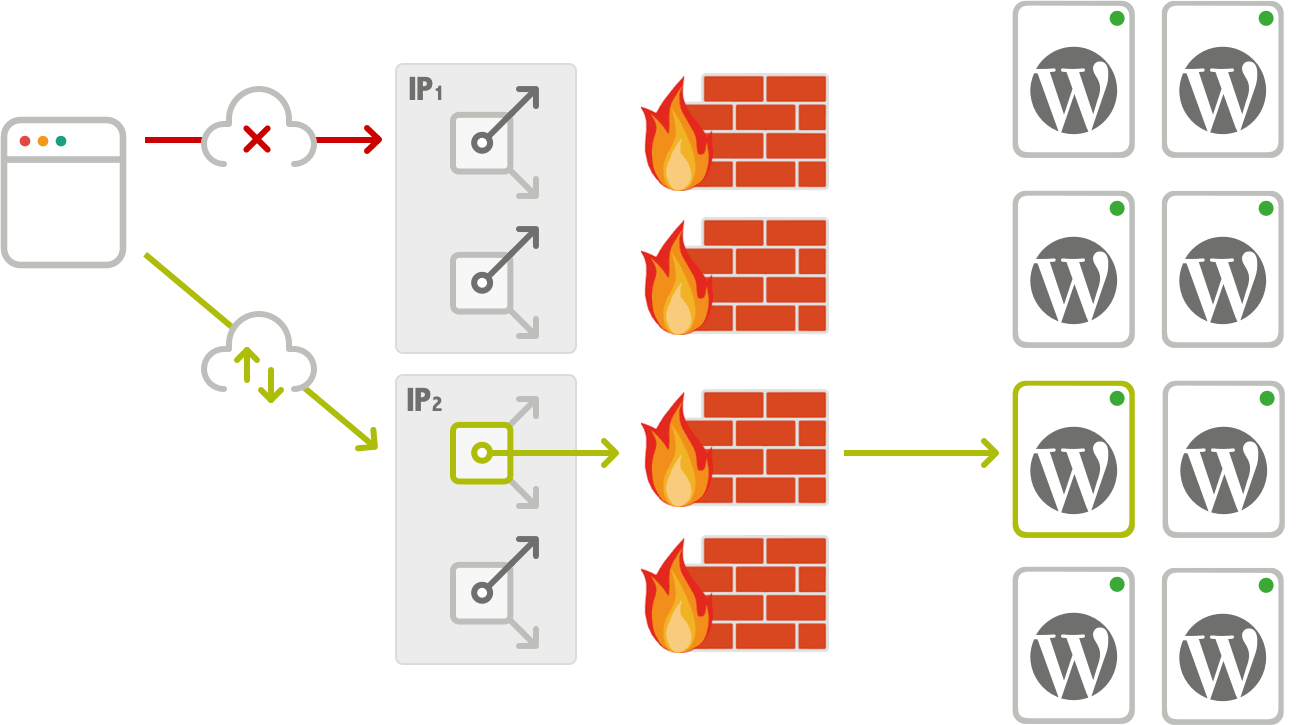
Bunker Guard: A Shared Security Policy Manager
At Wetopi, we have developed our own security policy system, Bunker Guard, designed to centralize rules and decisions from both our WordPress server network and external sources dedicated to security.
Bunker Guard analyzes the traffic directed to all Wetopi WordPress servers.
This knowledge is shared across all our entire network.
Firewalls adopt security measures dynamically, based on requests, and proactively, from previous experiences and from external sources dedicated to security.
And here is one valuable aspect: Our entire WordPress server network shares and takes advantage of this knowledge. In other words, when an attack to a WordPress website is identified and blocked, the filtering rule will protect all the Wetopi WordPress sites hosted at Wetopi.
Firewall blocking rules for WordPress
Our Bunker Guard is based upon two blocking techniques: the “Application Profiling”, based on current active traffic, and a second one called “external Blacklisting” based on external security sources.
Heuristic Application Profiling
We analyze all traffic requests to block those that don’t fit your WordPress application’s profile. The key is that Wetopi exclusively serves WordPress traffic.
Example: If a malicious crawler makes requests to see if your website uses Joomla, we directly block it.
At wetopi we only serve WordPress!
Serving exclusively WordPress traffic is one of our competitive advantages.
Signature Detection
Another common technique to block malicious requests is Signature Detection. All our network Incoming traffic is inspected before reaching a WordPress server. Using patterns and signature-based techniques, we block malicious requests and attack patterns.
Brute Force Attack Protection
By default, WordPress allows unlimited login attempts, which can leave your site vulnerable to brute force and dictionary attacks. Our firewall helps you mitigate this risk by limiting the number of login attempts.
Blacklisting from external sources
Thanks to All Cybercrime IP Feeds by FireHOL we keep permanently updated traffic blocking lists. These blacklists are mostly related to attacks, online services abusive, malwares, botnets, intrusion of servers and other activities related to cybercrime.
The blacklists are updated every minute, containing an average of 850,255,680 IP’s
Mitigation of DDoS attacks
Our data centers, have coverage for the mitigation of DDoS attacks through the use of selective filtering technology.
The selective method filters the received traffic, allowing only legitimate packets to pass to the WordPress servers, blocking illegitimate traffic.
DDoS analysis phase
To detect attacks, the traffic sent by the routers is monitored in real time. A continuous comparison of the signatures of the attacks is carried out. If similarities are detected, mitigation is activated automatically.
The analysis of the signatures is carried out in various protocols, such as: DNS, ICMP,”IP fragmentation”,”null” and”private”,”TCP null”, RST, SYN, ACK, UDP, …
DDoS aspiration phase
In order to channel a denial of service attack, a large network capacity is required to support the load. Thanks to the 15 Tbit/s network of our data center provider, the infrastructure is able to absorb a large amount of traffic in attacks. The total mitigation capacity is greater than 4 Tbit/s.
DDoS mitigation phase
Mitigation is the means and measures taken to mitigate the negative effects of a DDoS attack on a server. Mitigating is about filtering traffic to let only legitimate traffic through.
Mitigation combines different filters, each of which has a specific function. This technology diverts traffic to analyze it and only lets through legitimate traffic.
“Hack Free” Guarantee
As if all of the above were not enough, at wetopi we are committed to solving any security problem for free and immediately with the “Hack-free” guarantee included in our service policy.
To access the coverage of this guarantee it is necessary:
- Hire a plan that includes servers of “Medium” size or higher.
- Adopt basic precautions to protect yourself and your website from any Harmful or harmful content: it is necessary to keep up to date the updates that contain security patches in Extensions, Themes, and WordPress Core.
Security for WordPress requires a secure server
You probably already know that security does not end in that directory on the server where you have your WordPress hosted. And it is that the so-called service stack continues below your website served with WordPress.
There are many components and services that contribute to enlarging the angle of the so-called Attack Vector!
At wetopi we take care of the security of your server. By being able to work exclusively with WordPress we can efficiently automate the entire process of updating your server. In this other post we show you how we do this: basic rules for WordPress website security.
Don’t you have an account on Wetopi?
Free full performance servers for your development and test.
No credit card required.
This might also interest you: