2FA, an acronym for “Two-Factor Authentication”, implies that in addition to providing your username and password (first factor), an additional step (second factor) is required. This ensures the person trying to access a service is the legitimate user.
Two-Factor Authentication, or 2FA, enhances the security of restricted access services by asking the user for a second verification code, in addition to the password.
In this guide, we analyze its importance, the advantages and disadvantages of activating it, how to check if any of your passwords have been compromised, and how to activate it.
Other names for 2FA
There are numerous ways of referring to the two-factor authentication. Please take this into account for clarity:
- Double authentication factor.
- Second authentication factor.
- Two-phase authentication.
- Two-step authentication.
- Two-step identification.
- Two-step verification.
- Dual-Factor Authentication.
Is 2FA necessary?
The additional layer of security provided by Double Authentication addresses one of the most serious problems in the digital realm: credential theft. Although 2FA does not completely eliminate the risk of credential theft, it adds a crucial level of protection. This means that simply knowing a username and password is not enough to access a service.
Credential theft is something we should worry about: To give you an idea of the magnitude of the problem, in April 2023 a worldwide operation was carried out in 17 countries to dismantle the largest platform for selling access credentials to online services. They had the access data of about 2 million people, and the range of “prices” at which they sold the information made them accessible to a wide range of “customers” of the platform.
But, if you are using 2FA and your credentials are stolen, the thief will still need access to your second personal device, usually your mobile, where you normally receive the code sent by an authentication service.
Extra tip: Do not recycle or reuse the same password across different services.
Need to check if your password has been stolen? Check if your passwords have been compromised in this public database: https://haveibeenpwned.com/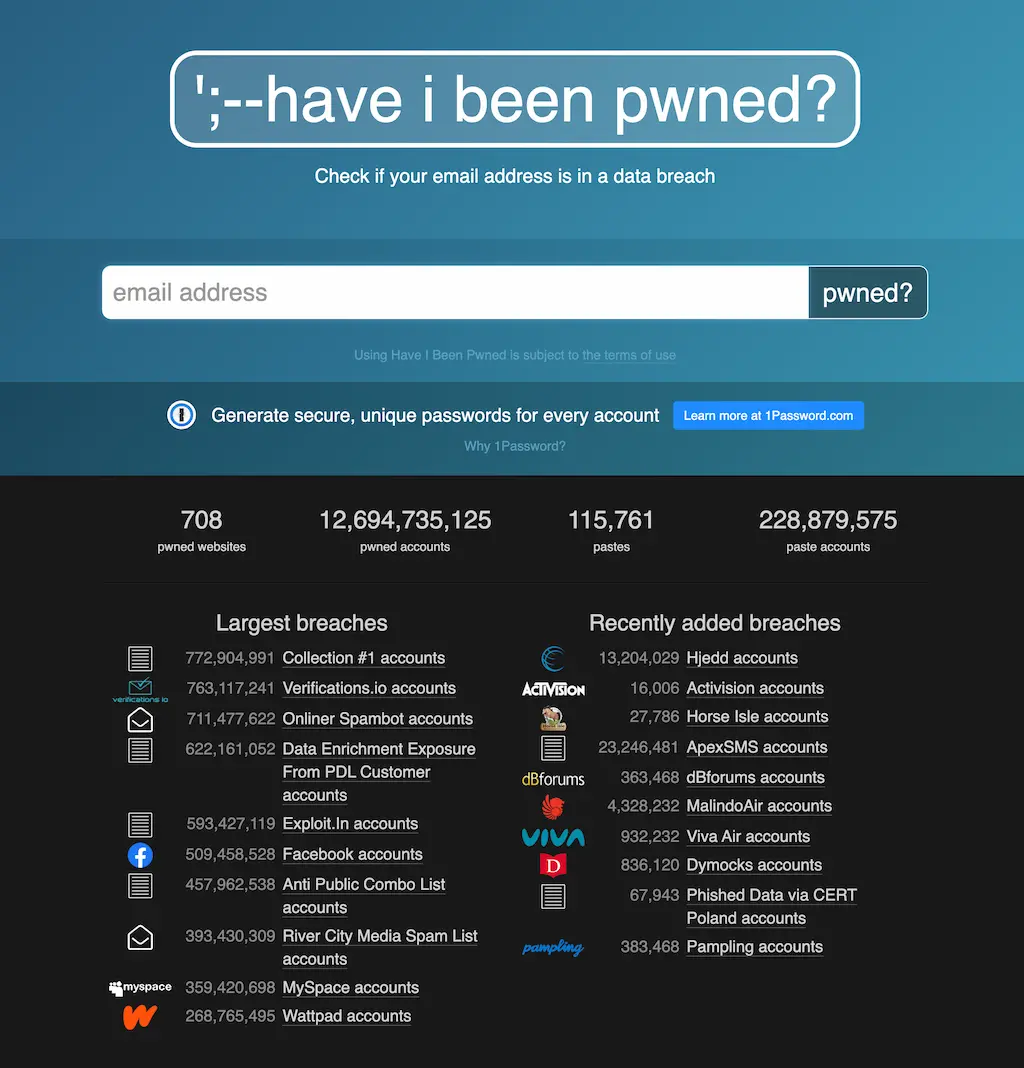
Disadvantages of 2FA
Two-Phase Authentication is certainly a valuable security feature, but it comes with some trade-offs:
- Introducing a second authentication factor is obviously an extra step when logging into your application or service.
- Implementing this second factor usually involves a mobile device. Therefore, if you don’t have your mobile device on hand, you won’t be able to access the service.
- If you use 2FA with One Time Passwords (OTP), it’s essential to maintain a backup of your secret key. This ensures access in situations where you might lose your device or, in more severe cases, when your heirs may require access to your accounts.
To reduce the friction associated with 2FA, some services, like Wetopi, employ a technique wherein they remember previously verified networks (IP addresses) and devices. This feature is highly beneficial and effectively mitigates many of the disadvantages associated with 2FA.
What is an authenticator application?
Authentication applications allow the generation of verification codes following a standard: the TOTP: “Time-Based One-Time Password Algorithm”.
This algorithm generates unique time-based passwords, meaning that each password is valid for only a short period of time before it expires. This timing increases security, reducing the risk of codes being intercepted and used maliciously. It is an additional layer of protection that, together with the traditional password, offers a more robust defense against unauthorized access. In case it expires a new code will be generated immediately after.
The “One Time Password” codes change every 30 seconds, and each service has its own sequence of digits.
Each sequence of OTP codes is generated from a seed or secret key
You will find multiple options, depending on the functionalities and platform. Some are dedicated exclusively to generating codes, such as “Google Authenticator”, and others cover not only the generation of “One-Time-Password” OTP codes, but also the broader task of managing and organizing passwords, such as “1Password”. or “LastPass”.
Recommended authentication apps
Below we indicate some of the best-known applications with validation code generation (sorted alphabetically):

1Password is a password manager that helps to securely store and manage passwords, credit card information, and other sensitive data in an encrypted vault. Its multi-platform, with years of proven experience and reputation, requires a paid subscription.
Bitwarden is a password manager that allows you to securely store and manage passwords, credit card details, and other sensitive information in an encrypted vault. It’s open-source, available on multiple platforms, and offers both free and premium subscription tiers. Note: Auth for 2FA is available only on paid plans.
Google Authenticator is a single purpose application used to manage all your 2FA codes. It’s free and available on multiple platforms.

LastPass is a password manager that enables you to securely store and manage passwords, credit card details, and other sensitive data in an encrypted vault. It’s available across multiple platforms, with years of proven experience and reputation, and offers both free and premium subscription options.

Microsoft Authenticator is akin to Google’s counterpart; it’s a dedicated application used to manage all your 2FA codes. It’s free and available on multiple platforms.
Twilio Authy is a dedicated 2FA app that’s free and available on multiple platforms. It allows users to secure the app with a PIN or biometric lock and offers an interface that’s especially suitable for managing a large number of accounts.
Two-Factor Authentication in Wetopi
If you are a wetopi customer, follow the steps below to activate Double Authentication on our hosting platform:
Activate 2FA Authentication
- If you are in the Wetopi panel, simply go to the security section in your profile menu:
- Once inside the security page, click on the “Enable two-factor authentication” button:
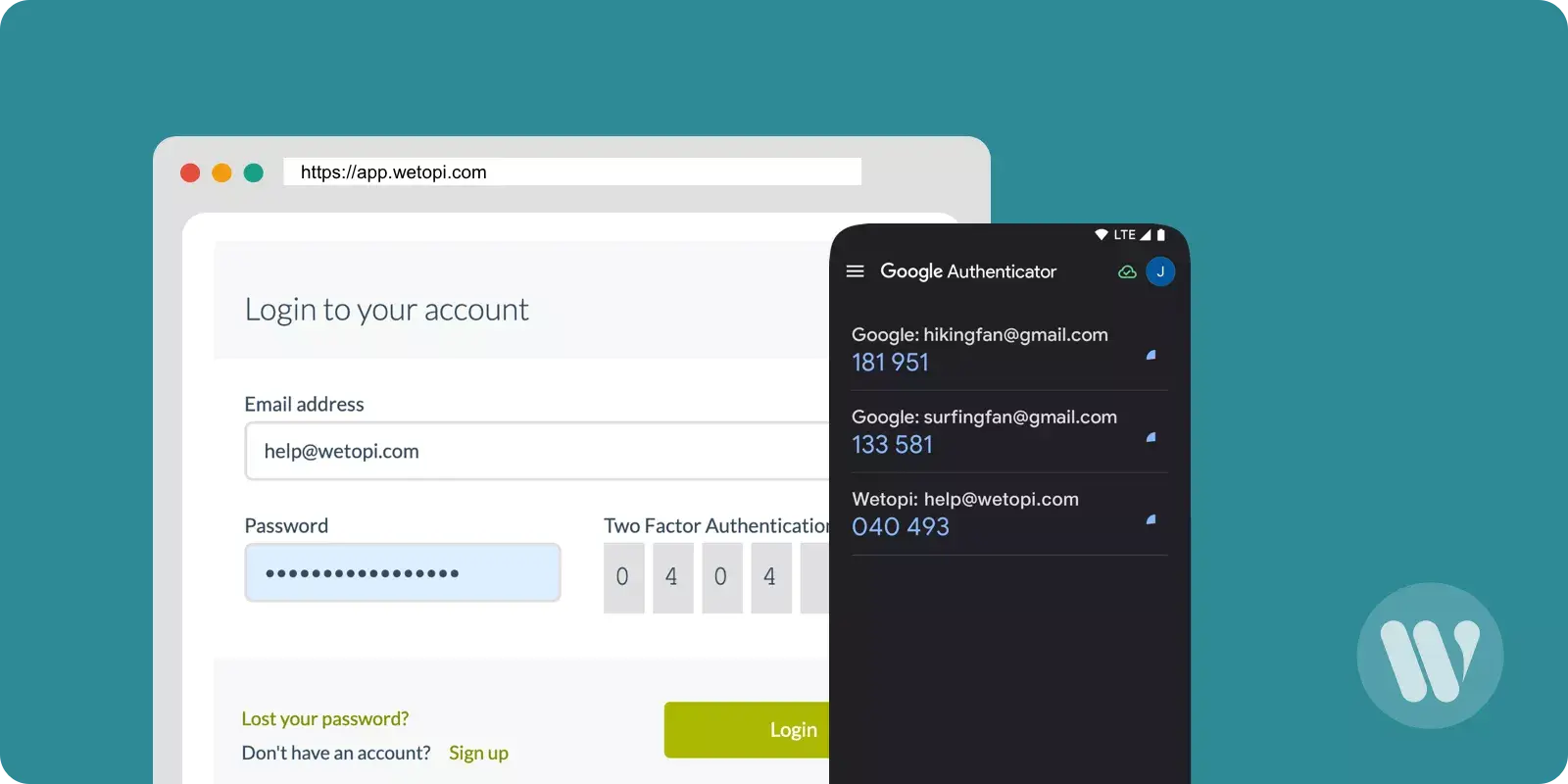
- Without changing the page, Wetopi will show you a QR code and a six-digit input field similar to the ones in this image:
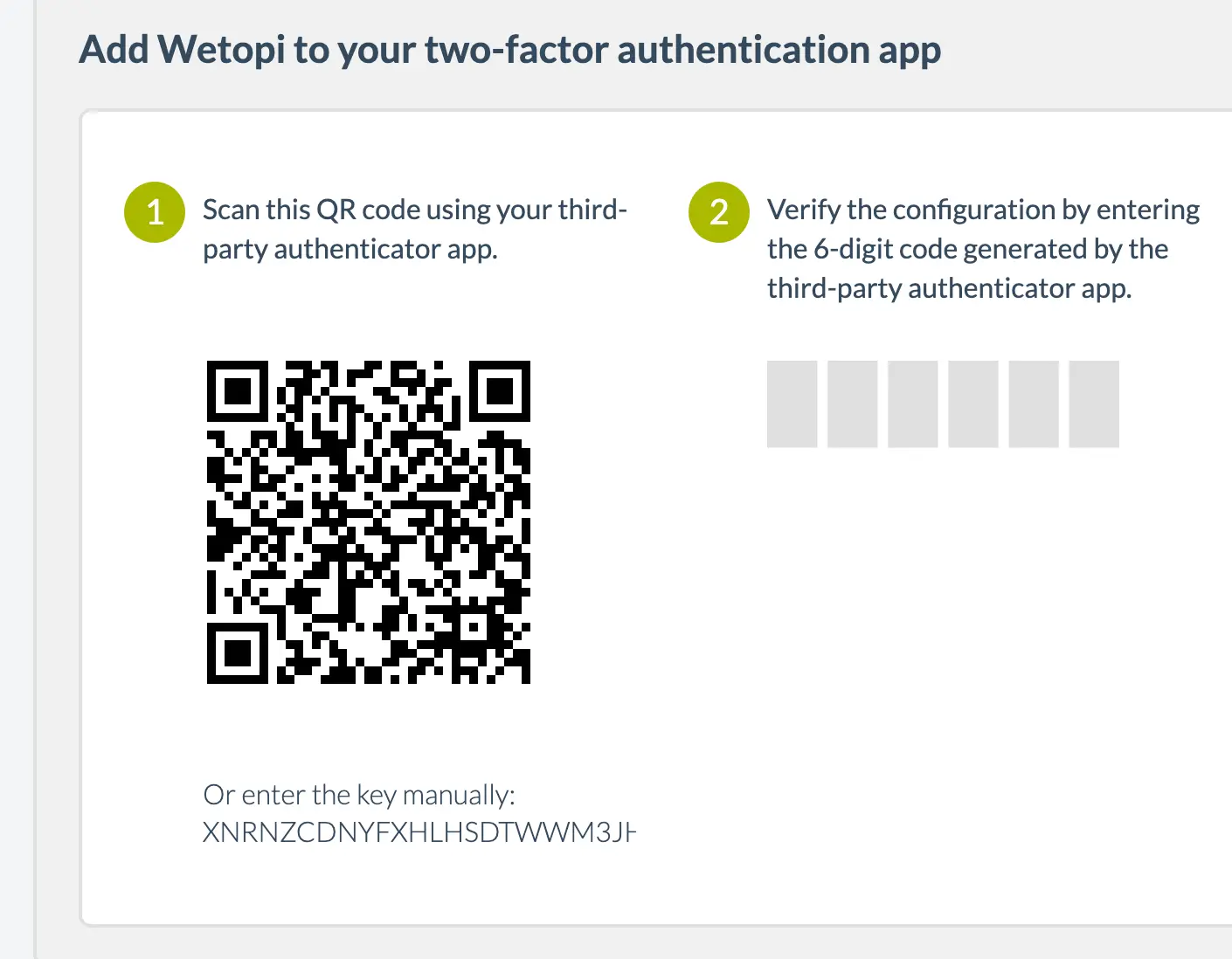
IMPORTANT: wetopi generates an exclusive code like the one shown in step 1 of the image.
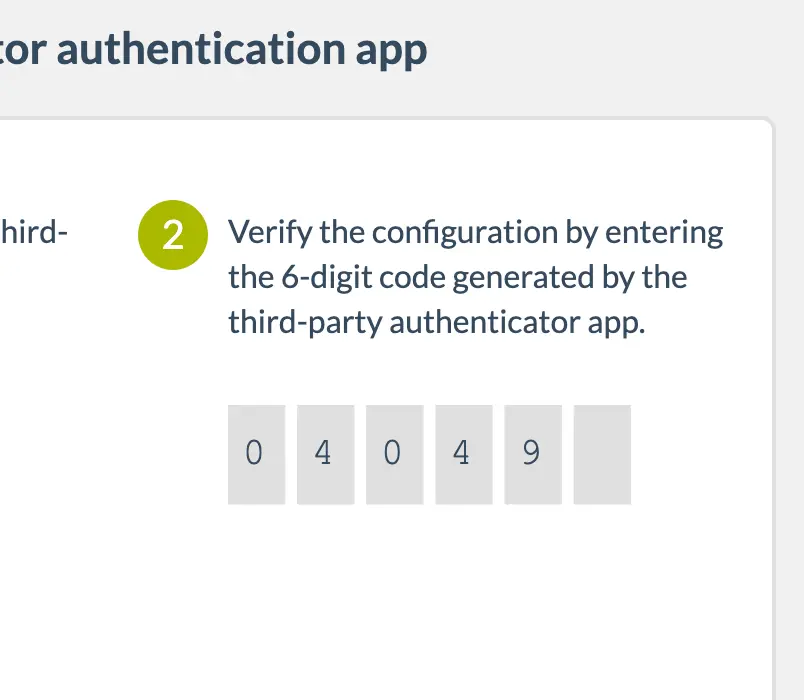
At this point, you’ll require an authenticator app. In this app, input the code generated by Wetopi. Subsequently, the application will generate a valid verification code, which you should input as illustrated in step 2 of the aforementioned image.
The process of registering a service in the different applications may have small variations, but it will follow a basic pattern. We explain it to you below:
Add the code to your app
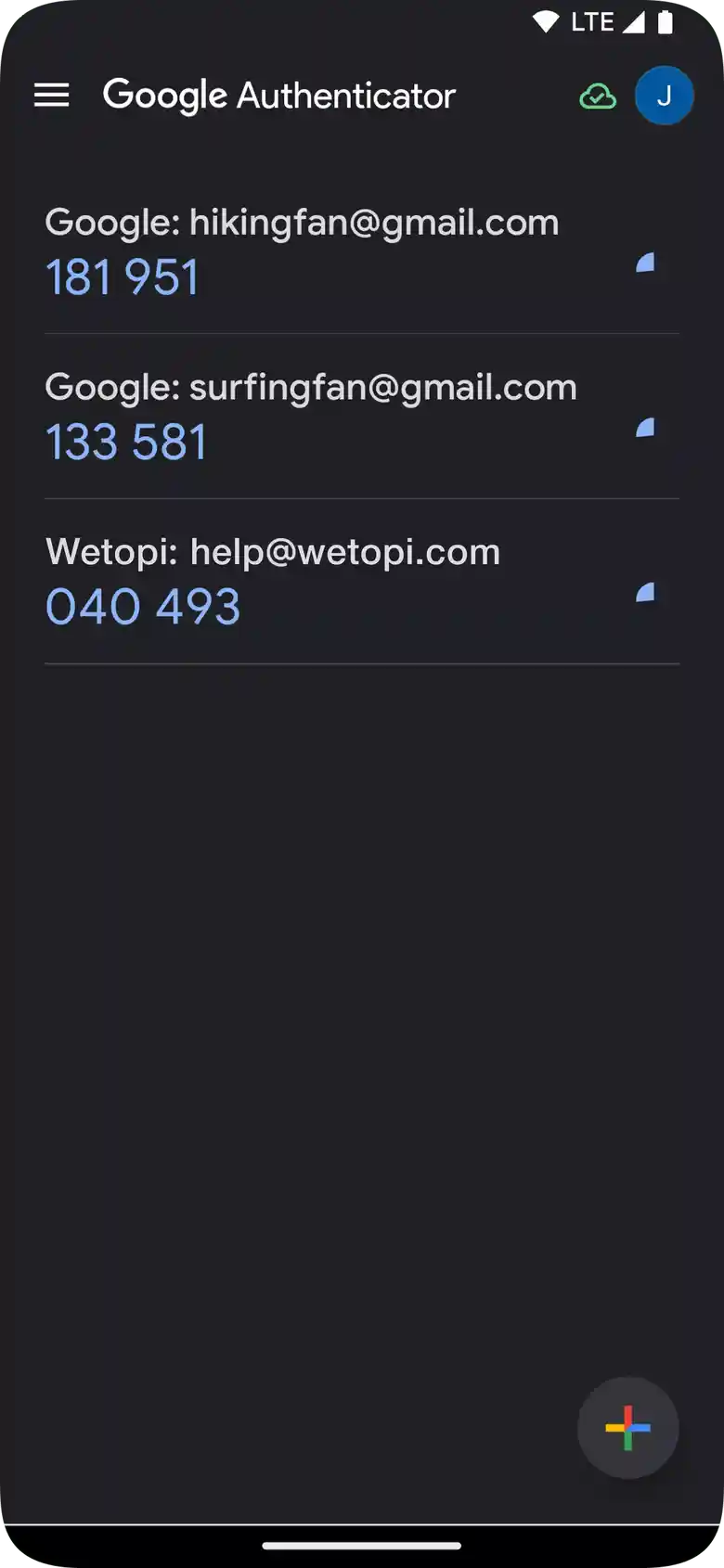
The wetopi service will have generated an exclusive secret code for you, as we have shown you in the previous step. To register this code, for example, in Google Authenticator, click on the “+” sign
After registering the code, a new code generator identified, for example, as “Wetopi: help@wetopi.com” will appear on your application screen.
Enter the code generated by your application
To finish confirming the activation of 2FA in wetopi, stay in the “my security” section. Now you must enter the code generated by the authentication application in which you registered the wetopi account.
In our example, following what “Google Authenticator” indicates, we enter the code “040 493” in step 2.
2FA will appear upon login
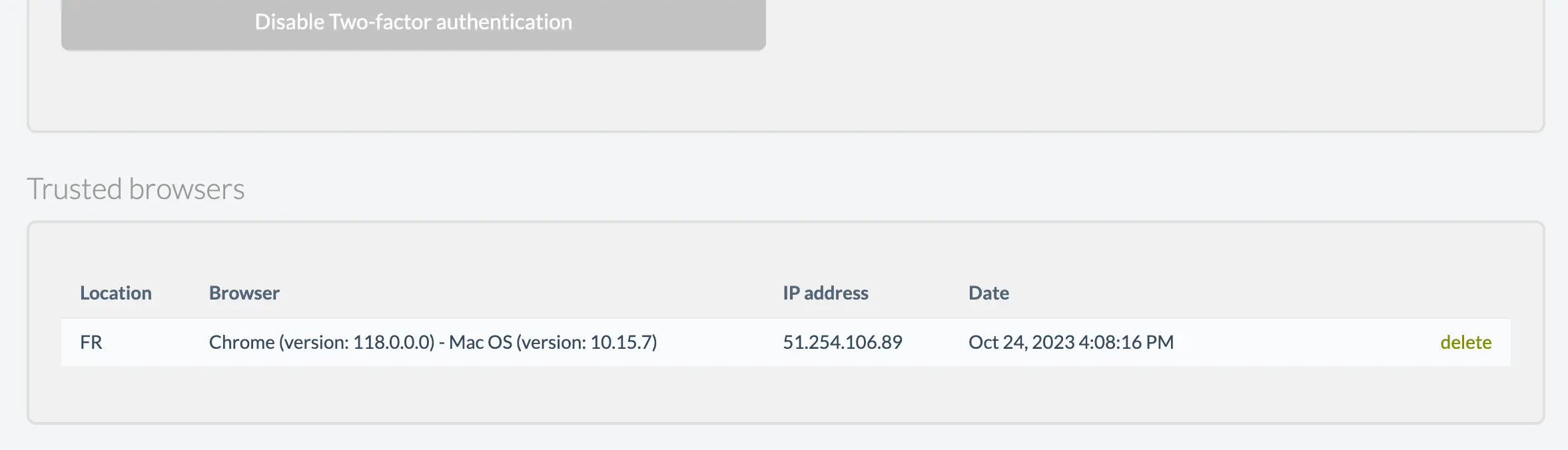
After activating double authentication, the browser and the IP address from which we have validated are registered in Wetopi:
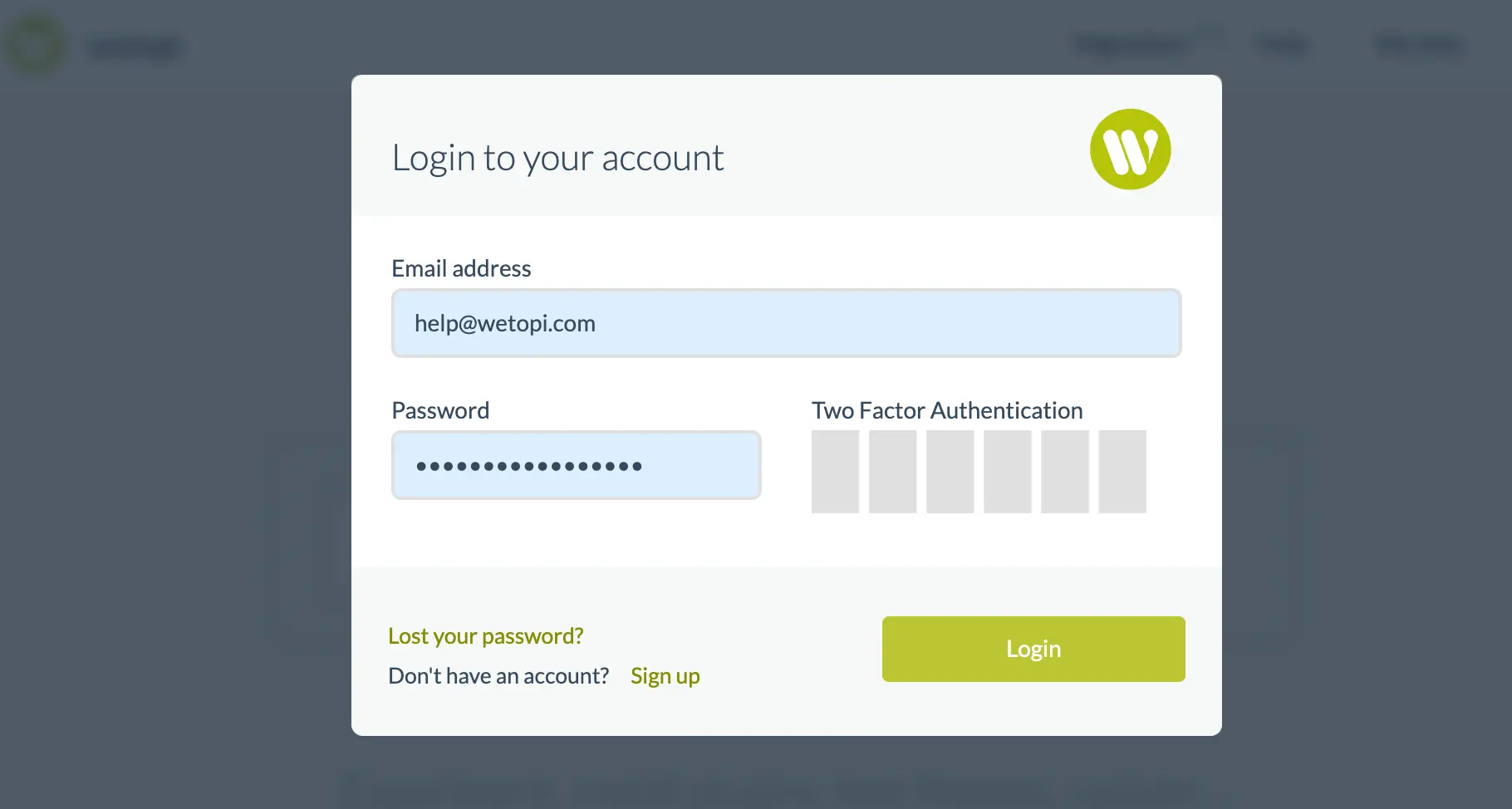
If when we log in we do it from an unknown browser, or from a new location (a new IP address), Wetopi will alert us and ask us for the code generated by our authentication application:
Conclusion
In conclusion, two-factor authentication, commonly referred to as 2FA, offers an enhanced layer of security in our increasingly digital world. While it might introduce an additional step to the login process, the trade-off is a significant boost in protection against unauthorized access. Tools like Microsoft Authenticator and Google’s counterpart provide user-friendly means to adopt this essential security measure.
As cyber threats continue to evolve, embracing such safeguards is more critical than ever!
Don’t you have an account on Wetopi?
Free full performance servers for your development and test.
No credit card required.
This might also interest you: