In this post we analyze precisely the “when” and “why” to disable XMLRPC and how to do it efficiently.
Remote access to WordPress using XMLRPC has been made easy for many years. Sending HTTP requests to xmlrpc.php allows you to send commands to WordPress and manage its content without login into the desktop.
However, XMLRPC has its downsides. Sometimes introduces security vulnerabilities and has now been superseded by the WordPress API.
What is XMLRPC?
In the root directory of every WordPress site, you will find a file named xmlrpc.php. It was created to provide a way for WordPress sites to communicate with each other and for other applications to communicate with WordPress.
XML is the encoding mechanism used for data exchange and RPC is the communication mechanism. RPC stands for Remote Procedure Call.
The WordPress XMLRPC Relay
While WordPress XMLRPC remote access has been around for many years, the WordPress API has long since evolved into a more robust and secure solution.
With the new WordPress API, the use of XML-RPC has been completely outdated. If you don’t need XMLRPC for any of the features explained below, it’s best to disable XMLRPC entirely. We can assure you that you will avoid the numerous security problems that access to this file entails.
The new API is not perfect, but it does provide a more secure and robust solution to the WordPress login problem.
Currently, the developer community is abandoning the use of xmlrpc.php
Can I disable the XMLRPC of my WordPress?
XMLRPC access is still used in remote management from WordPress.com when using the Jetpack plugin or services like Zapier, IFTTT.
Jetpack still drags remote management using access to
xmlrpc.php
Also, the Pingbacks functionality or some of the Apps like the official WordPress mobile app use xmlrpc.php to interact with WordPress.
But… Who manages WordPress posts today from mobile? Well, if you are one of those who love the mobile world, it is better that you use the browser of your device to access the administrator of your WordPress. After all, it is more secure, and its “responsive” interface works perfectly.
Why disable xmlrpc.php?
Access to WordPress XMLRPC, by offering advanced management features, becomes attractive to an attacker. That is why disabling XMLRPC will help us to reduce significantly the angle of the so-called Attack Vector.
The types of attack to which xmlrpc.php is usually exposed are:
Brute force attack against XMLRPC
In general, the brute force attack is used to obtain the username and password combination through massive requests, that is why it is called “brute force”.
As XMLRPC is protected by username and password in operations that modify data, requests to xmlrpc.php are an ideal destination to try to find credentials.
To carry out a brute force attack, it is enough to make consecutive xmlrpc.php calls trying different users and passwords as parameters.
Amplified attack
The amplified attack is an even more dangerous variant of the brute force attack. In a brute force attack, each attempt to try a username and password results in a request. On the other hand, in the amplified attack, tens of thousands of combinations can be tried in the same request. However, this vulnerability is currently fixed.
DDoS attacks using XMLRPC
DDoS attacks, “Distributed Denial of Service”, are extremely difficult to avoid, nobody can say that they are free from them. However, it is important not to make things easy. The basis of a DDoS attack is to overwhelm your server by making many simultaneous requests.
If we take into account that:
- xmlrpc.php is capable of interfacing with WordPress, making heavy use of the database.
- It can hardly be cached to prevent it from using too many server resources.
- It has features such as Pingback that make it easy to distribute the sending of requests.
The sum of these factors makes xmlrpc.php the perfect tool for the attacker.
Disable WordPress XMLRPC
To completely disable XMLRPC, our advice without a doubt is to do it at the server level and avoid the use of extensions.
Blocking its access at the webserver level is the most efficient, as we prevent requests from being executed in WordPress.
Keep in mind that any request that comes to WordPress represents dynamic execution of php code and database queries.
If you are hosting your site with Wetopi, you can do this with a single click.
Disabling xmlrpc.php at Wetopi
At Wetopi, you can enable and disable the access to xmlrpc.php of your WordPress with a single click.
You’ll find this option in the WordPress server Menu, inside the advanced options section. By default at Wetopi you’ll find XmlRPC access disabled like shown in this image:
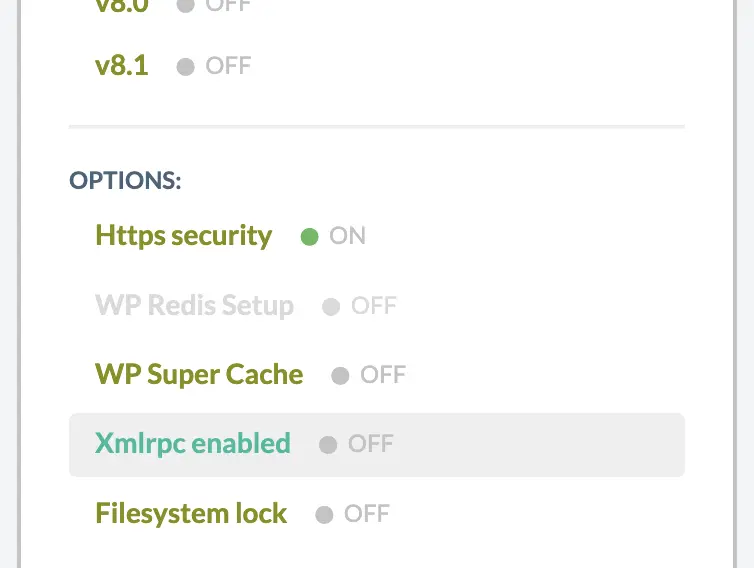
Now, with “Xmlrpc enabled” OFF, If you try to access the xmlrpc.php the browser will answer with a HTTP Error 403 Forbidden:
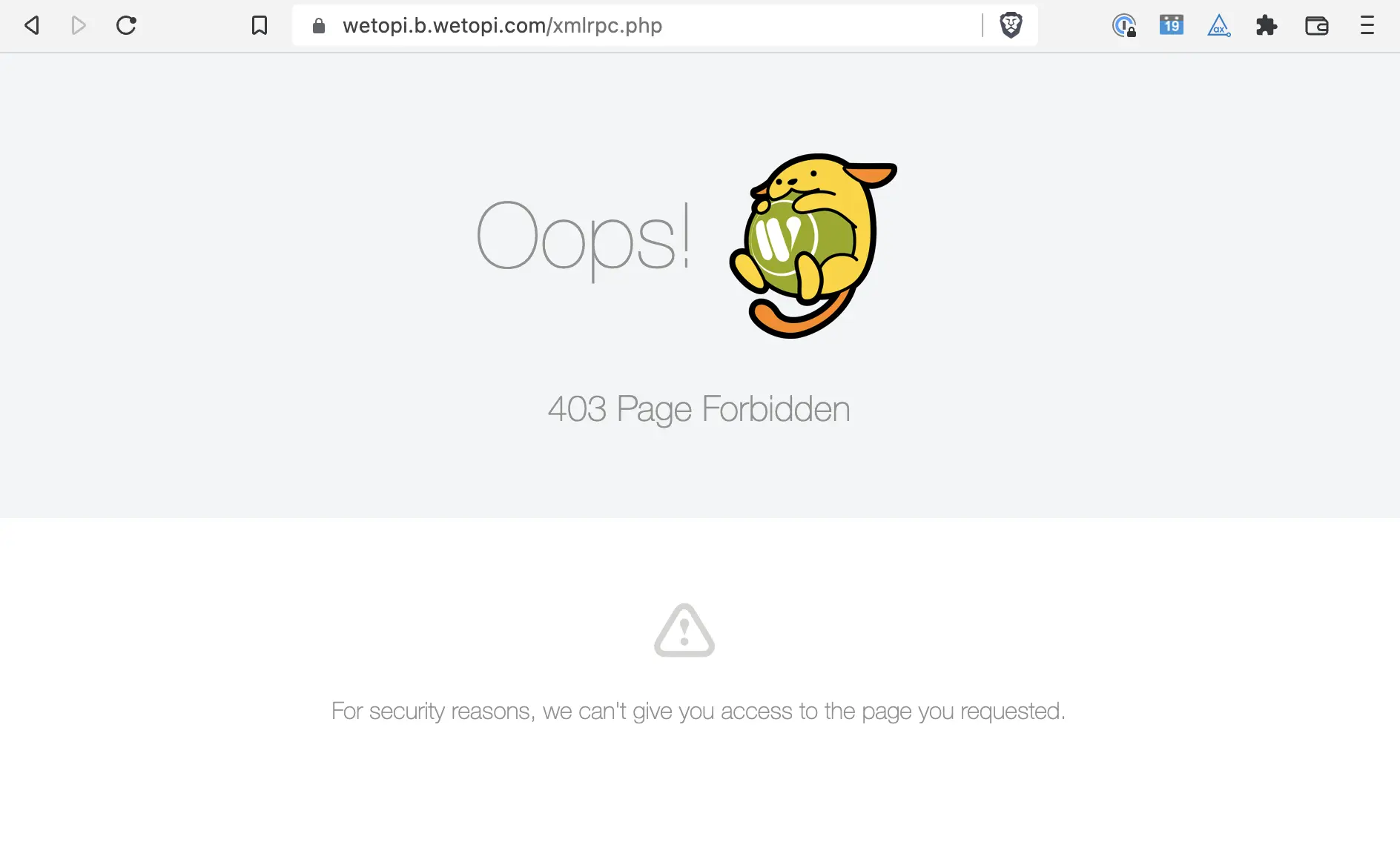
If you need a WordPress with XmlRPC access, simply click over “Xmlrpc enabled” to switch-on the access to this page.
Test how to block WordPress XMLRPC requests without breaking your production website.
If you don’t have a development WordPress server, signup at wetopi, it’s FREE
When testing new server configurations, it is highly recommended to work on a “localhost” or “Staging” server.
Behind the scenes
When you disable XmlRPC in your Wetopi WordPress server, we leave the file /var/www/conf/nginx-disable-xmlrpc.conf with the mentioned code, thus nginx includes it when loading the configuration..
Below we show all the details if you want to reproduce the process completely manually on Nginx or Apache servers.
Manually disable xmlrpc.php in Nginx
If you run nginx as your web page server, you will need to locate the nginx configuration files. The common filesystem place in Linux is /etc/nginx.conf
Here at wetopi, as WordPress specialized hosting, we also use Nginx. In our servers, you can find the configuration file in /var/www/conf/nginx.conf
Once you have opened the file appropriate configuration file, add these lines into the server section along with your other “location” :
# denaying access to WordPress xmlrpc:
location = /xmlrpc.php {
deny all;
access_log off;
log_not_found off;
return 403;
}IMPORTANT: with Wetopi, you don’t need to manually modify Nginx config files. XmlRPC can be disabled and enabled from your control panel with a single clic.
Load the new Nginx configuration
After any Nginx configuration modification, it’s always necessary to reload the config.
In an installation where you manage the Nginx server, open a shell and launch the reload config command:
# Test config before reload:
nginx -t
# Reload nginx:
nginx -s reload
Manually disable xmlrpc.php in Apache
The first step is to locate the .htaccess file at the root of your WordPress site. This is the only file we will need to edit to disable XMLRPC access.
One way to access and edit these files is to securely connect to the server via SFTP.
Once you’ve opened the .htaccess file, add these lines to the end and save your changes.
<Files xmlrpc.php>
order deny, allow
deny from all
</Files>
Conclusion
Xmlrpc.php was developed to provide remote management functionality to your WordPress site. Due to its remote access functionality, it has become the target point of numerous intrusion and DDoS attacks.
Today, the new WordPress API provides these features without sacrificing security. Our recommendation, if you don’t depend on Jetpack, Zapier, or IFTTT remote management, disable it as soon as you can.
Don’t you have an account on Wetopi?
Free full performance servers for your development and test.
No credit card required.
